RBAC Roles
- Authors
- Name
- Michael Bui
Overview
Documentation: Microsoft Docs
RBAC (Role Based Access Control) helps manage who has access to Azure Resources. You assign RBAC roles to a security principal to restrict the amount of permissions it has.
In this lab, we'll be using the following lab structure below provided by Microsoft Learning
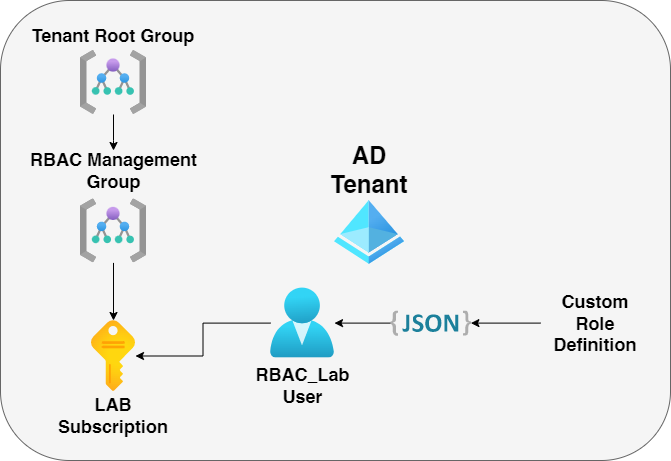
- We have a RBAC Management group & lab subscription already created.
- We'll create a custom role definition that only allows the user to read
resource groups& manage support requests only inside theLAB subscription
Instructions
Custom RBAC Role
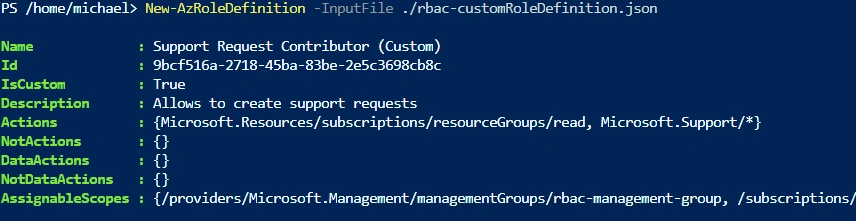
- Role Definition
{
"Name": "Support Request Contributor (Custom)",
"IsCustom": true,
"Description": "Allows to create support requests",
"Actions": [
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Support/*"
],
"NotActions": [
],
"AssignableScopes": [
"/providers/Microsoft.Management/managementGroups/rbac-management-group",
"/subscriptions/SUBSCRIPTION_ID"
]
}
- Open cloud shell and upload the .json custom role
Assigning Role
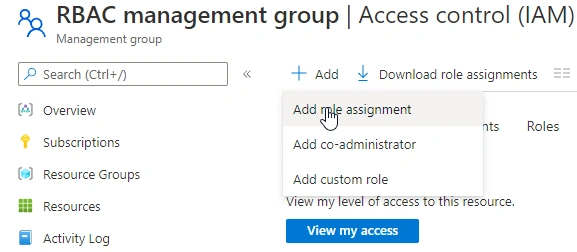
We have created a user named RBAC_Lab_User for this lab
- Go to the RBAC management group -> Add -> Role Assignment
- Search for our created custom role
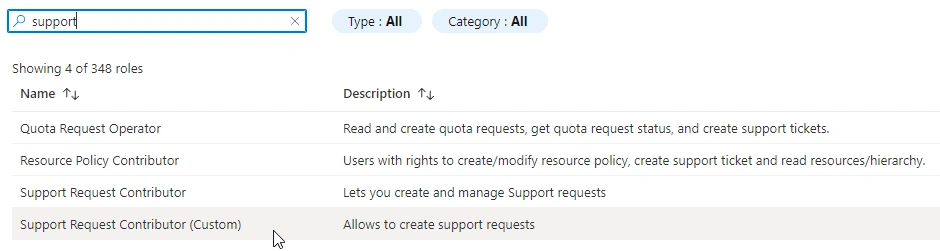
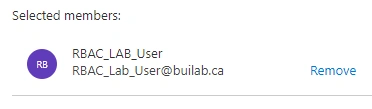
- Select the RBAC Lab user
Verification
- Log in as RBAC Lab User
- Browse to
Resource Groups - We can confirm that there are no resource groups

- Using a global admin, create a resource group with a storage account resource inside
- Now back on RBAC Lab User we can see the resource group
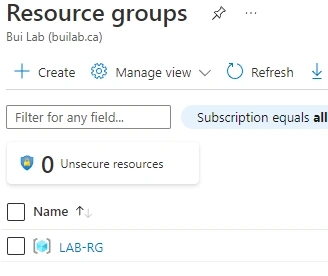
- However, we still do not see resources on our RBAC Lab User account